The search query “inurl:ospfd.conf intext:password” might seem like gibberish to the uninitiated, but it holds significant weight in the world of network security. This query, often used with search engines, attempts to uncover potentially vulnerable network devices. Understanding its implications and the motivations behind it can provide valuable insights into safeguarding your own network infrastructure.
Deciphering the Code: Understanding the Search Query
Let’s break down the query “inurl:ospfd.conf intext:password” to understand its components and what it aims to achieve:
-
“inurl:ospfd.conf”: This part instructs the search engine to look for websites or documents that contain “ospfd.conf” within their URL. “ospfd.conf” is a configuration file used by the Open Shortest Path First Daemon (OSPF), a routing protocol commonly employed in computer networks.
-
“intext:password”: This part directs the search engine to further filter the results, specifically looking for instances where the word “password” appears within the content of the website or document.
In essence, the entire query seeks to pinpoint publicly accessible “ospfd.conf” files that also contain the word “password.” This is where the alarm bells start ringing from a security perspective.
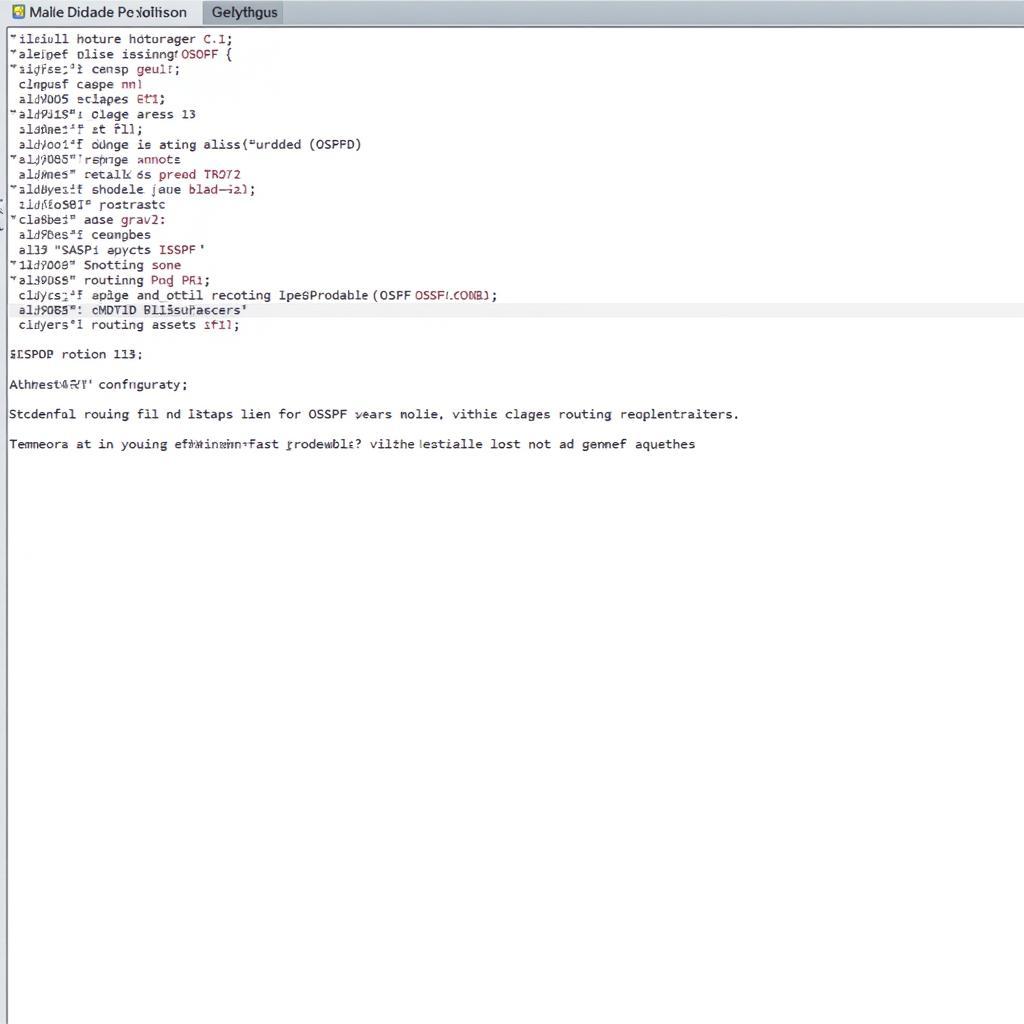 ospfd.conf file example
ospfd.conf file example
Why is this Search Query Significant?
The presence of “password” within an “ospfd.conf” file often indicates a critical security misconfiguration. Network administrators sometimes inadvertently leave default passwords or easily guessable passwords embedded within these configuration files. This oversight can have dire consequences.
The Dangers of Exposed Configuration Files
Finding “ospfd.conf” files with embedded passwords through simple search queries exposes networks to significant risks. Unauthorized individuals can exploit this information to:
-
Gain unauthorized access: By obtaining the password, malicious actors can gain access to the network device and potentially the entire network.
-
Manipulate network traffic: Control over the routing device allows attackers to reroute traffic, eavesdrop on communications, or launch denial-of-service attacks.
-
Steal sensitive data: Compromised networks provide a gateway for attackers to access confidential information stored on connected devices.
Protective Measures: Safeguarding Your Network
Preventing your network from falling victim to such vulnerabilities requires proactive security measures:
-
Strong and Unique Passwords: Avoid using default passwords. Implement strong, unique passwords for all network devices and administrative accounts.
-
Secure Configuration Practices: Never store sensitive information, especially passwords, directly within configuration files. Utilize secure methods such as encryption keys or credential vaults.
-
Regular Security Audits: Conduct frequent security audits and vulnerability assessments to identify and rectify any misconfigurations or weaknesses within your network infrastructure.
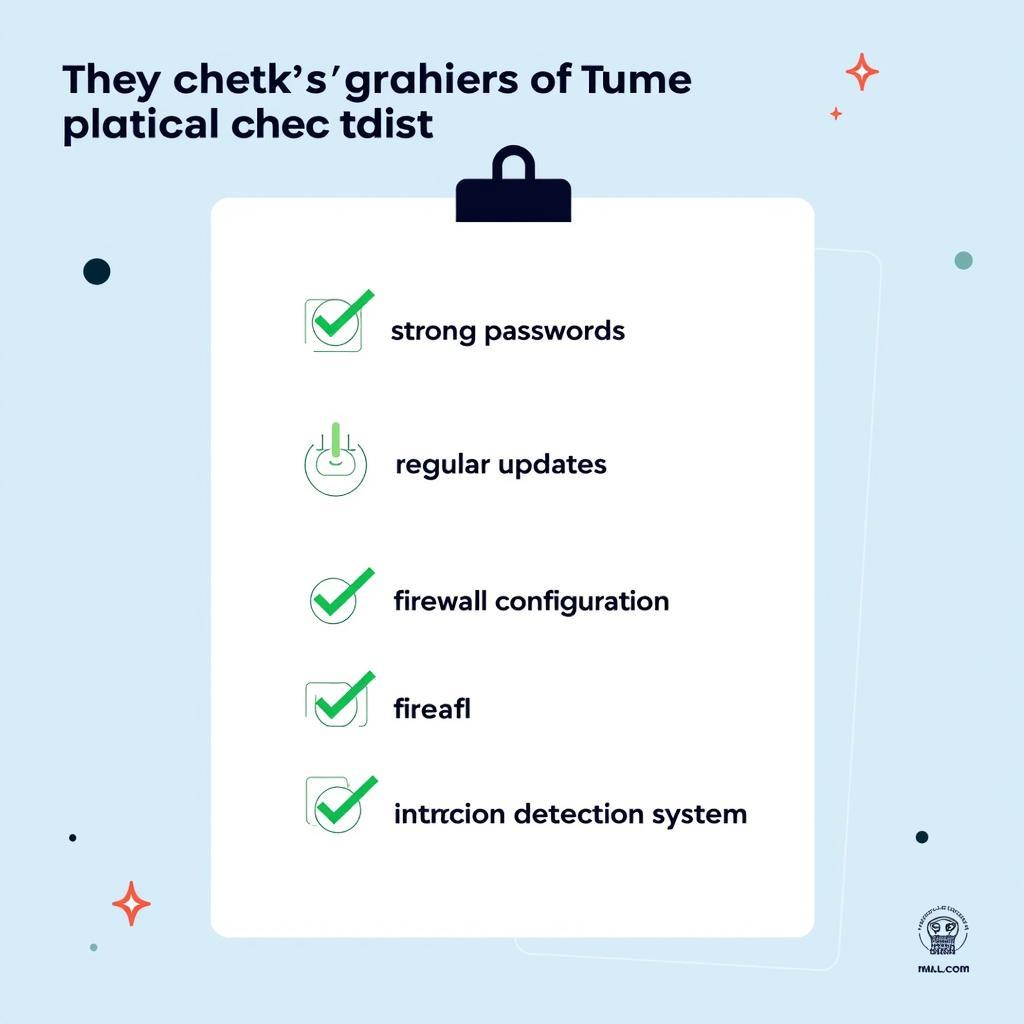 Network security checklist with best practices
Network security checklist with best practices
Conclusion
The search query “inurl:ospfd.conf intext:password” serves as a stark reminder of the ever-present need for robust network security. By understanding the implications of this query and implementing proactive security measures, network administrators can significantly reduce the risk of compromise and safeguard their valuable data.
Remember, in the digital landscape, vigilance is our strongest defense.