ESET Endpoint Encryption, formerly known as DESlock+, offers robust protection against data breaches, ensuring your sensitive information remains confidential even if your device is lost or stolen. This guide delves into the intricacies of ESET Endpoint Encryption, exploring its features, benefits, and the download process.
Understanding the Importance of Endpoint Encryption
In an era defined by digital transformation, safeguarding sensitive data is paramount. Endpoint encryption emerges as a critical line of defense, particularly as traditional perimeter security measures prove increasingly inadequate against sophisticated cyber threats.
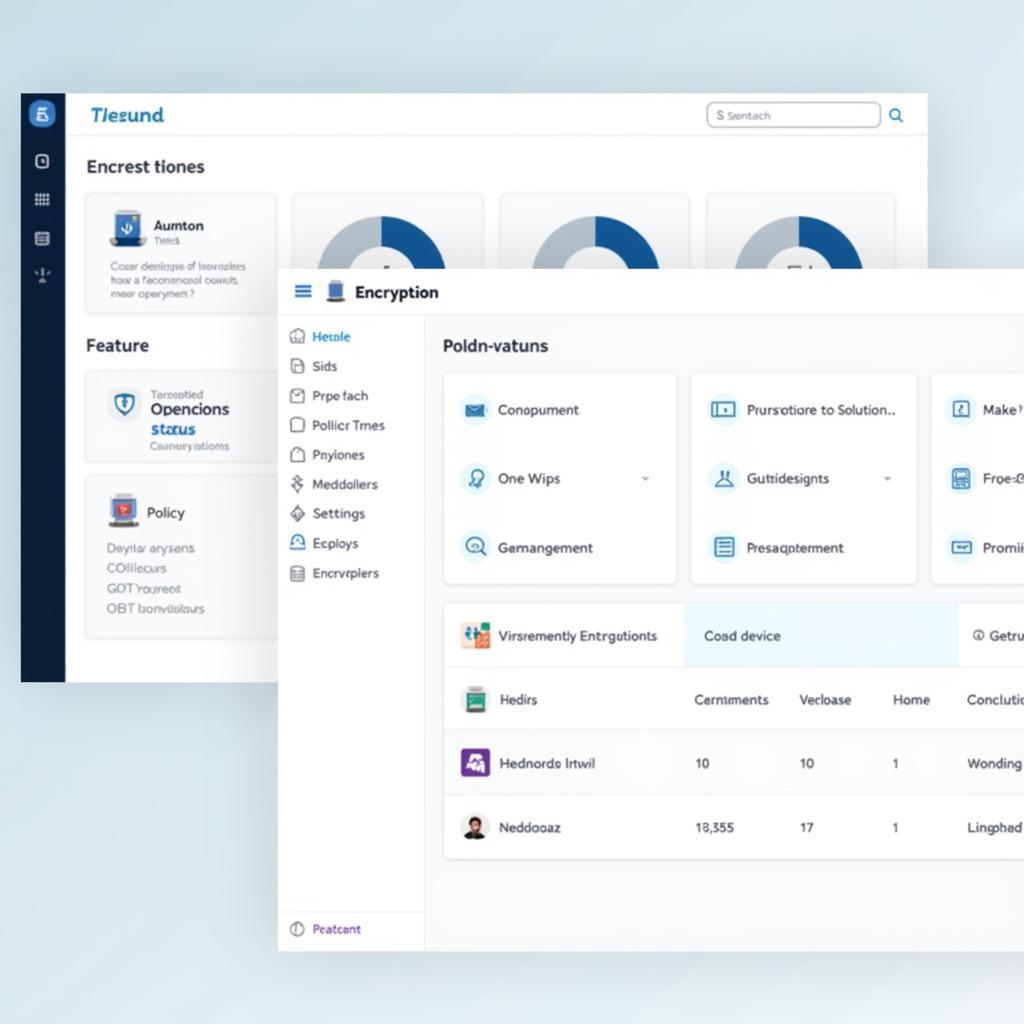 ESET Endpoint Encryption Dashboard
ESET Endpoint Encryption Dashboard
By encrypting data at the device level, ESET Endpoint Encryption ensures that even if a device falls into the wrong hands, the information remains inaccessible without proper authorization. This proactive approach to data security mitigates the risk of data breaches, protecting your organization’s reputation and ensuring compliance with regulatory standards.
Key Features and Benefits of ESET Endpoint Encryption
ESET Endpoint Encryption stands out for its comprehensive suite of features designed to provide robust endpoint protection:
- Full-Disk Encryption (FDE): Encrypt your entire hard drive, including the operating system, applications, and data, ensuring complete protection against unauthorized access.
- Removable Media Encryption: Securely encrypt USB drives, external hard drives, and other removable media, preventing data leaks through portable devices.
- File and Folder Encryption: Encrypt specific files and folders, adding an extra layer of security to sensitive information stored on shared devices or in the cloud.
- Pre-Boot Authentication: Enforce strong authentication at the pre-boot level, requiring users to enter their credentials before the operating system loads, preventing unauthorized access from the outset.
Beyond its robust encryption capabilities, ESET Endpoint Encryption offers several benefits:
- Centralized Management: Manage encryption policies, user access, and device security from a central console, streamlining administration and ensuring consistent security enforcement across your organization.
- User-Friendly Interface: The intuitive interface simplifies encryption and decryption tasks, minimizing user disruption and ensuring a seamless experience.
- Compliance Readiness: Meet industry-specific compliance requirements, such as GDPR, HIPAA, and PCI DSS, with comprehensive encryption and auditing capabilities.
How to Download ESET Endpoint Encryption
To download ESET Endpoint Encryption, follow these steps:
- Visit the official ESET website and navigate to the “Business” section.
- Select “Endpoint Encryption” from the list of products.
- Choose the edition that best suits your needs, considering factors such as the number of devices and desired features.
- Click on the “Download” button to initiate the download process.
Once the download is complete, follow the on-screen instructions to install and configure ESET Endpoint Encryption on your devices.
ESET Endpoint Encryption: Frequently Asked Questions
Q1: Is ESET Endpoint Encryption compatible with my operating system?
ESET Endpoint Encryption supports a wide range of operating systems, including Windows, macOS, and Linux. Check the system requirements on the ESET website to ensure compatibility with your specific devices.
Q2: What happens if I forget my encryption password?
ESET Endpoint Encryption provides recovery options, such as recovery keys and user self-service portals, to regain access to encrypted data in case of password loss.
 ESET Endpoint Encryption Compatibility
ESET Endpoint Encryption Compatibility
Q3: Can I manage ESET Endpoint Encryption remotely?
Yes, ESET Endpoint Encryption offers centralized management capabilities, allowing administrators to remotely deploy, configure, and monitor encryption policies and device status from a central console.
Conclusion
ESET Endpoint Encryption emerges as an essential tool in today’s data-driven landscape. By encrypting sensitive information at the device level, organizations can effectively mitigate the risk of data breaches, ensuring business continuity and protecting their reputation. With its comprehensive features, centralized management, and user-friendly interface, ESET Endpoint Encryption provides a robust and scalable solution for securing your endpoints and safeguarding your valuable data. Contact our team at 0966819687, email us at [email protected], or visit our office located at 435 Quang Trung, Uông Bí, Quảng Ninh 20000, Vietnam for 24/7 support. We also encourage you to explore our other helpful articles for more insights.