Looking for a comprehensive guide on social engineering? Want to explore the depths of this intriguing field through a well-structured table of contents? You’ve come to the right place! This article delves into the world of social engineering, providing valuable insights and resources, including potential avenues to access a “Social Engineering Table Of Contents Pdf Free Download.”
Understanding Social Engineering: Beyond the Surface
Social engineering, often described as the art of human hacking, goes beyond technical vulnerabilities to exploit the human element within organizations and systems. This tactic leverages psychological manipulation, deception, and influence to trick individuals into divulging confidential information or granting unauthorized access.
Instead of relying on brute force or complex coding, social engineers use clever tactics to prey on human weaknesses like trust, helpfulness, and fear. Imagine receiving an email seemingly from your bank, urging you to update your login credentials. An unsuspecting click could lead you to a fake website designed to steal your information. This, in essence, is the crux of social engineering.
 social engineering attack example
social engineering attack example
Delving into the Table of Contents: A Glimpse into the World of Social Engineering
A well-structured “social engineering table of contents pdf” can offer a structured roadmap to this captivating domain. It can unveil a treasure trove of knowledge, from understanding various psychological principles exploited by these tactics to dissecting different attack vectors.
Let’s visualize a potential structure for such a resource:
Section 1: Introduction to Social Engineering
- Definition and Historical Context
- Psychology Behind Social Engineering: Exploiting Human Vulnerabilities
- Legal and Ethical Implications
Section 2: Types of Social Engineering Attacks
- Phishing: Casting a Wide Net
- Baiting: Tempting with Irresistible Offers
- Pretexting: Creating Believable Scenarios
- Quid Pro Quo: Offering Something in Return
- Tailgating: Slipping Through the Cracks
Section 3: Methodology of a Social Engineer
- Reconnaissance: Gathering Intelligence
- Developing Trust and Rapport
- Exploitation: Executing the Attack
- Covering Tracks: Evasion and Obfuscation
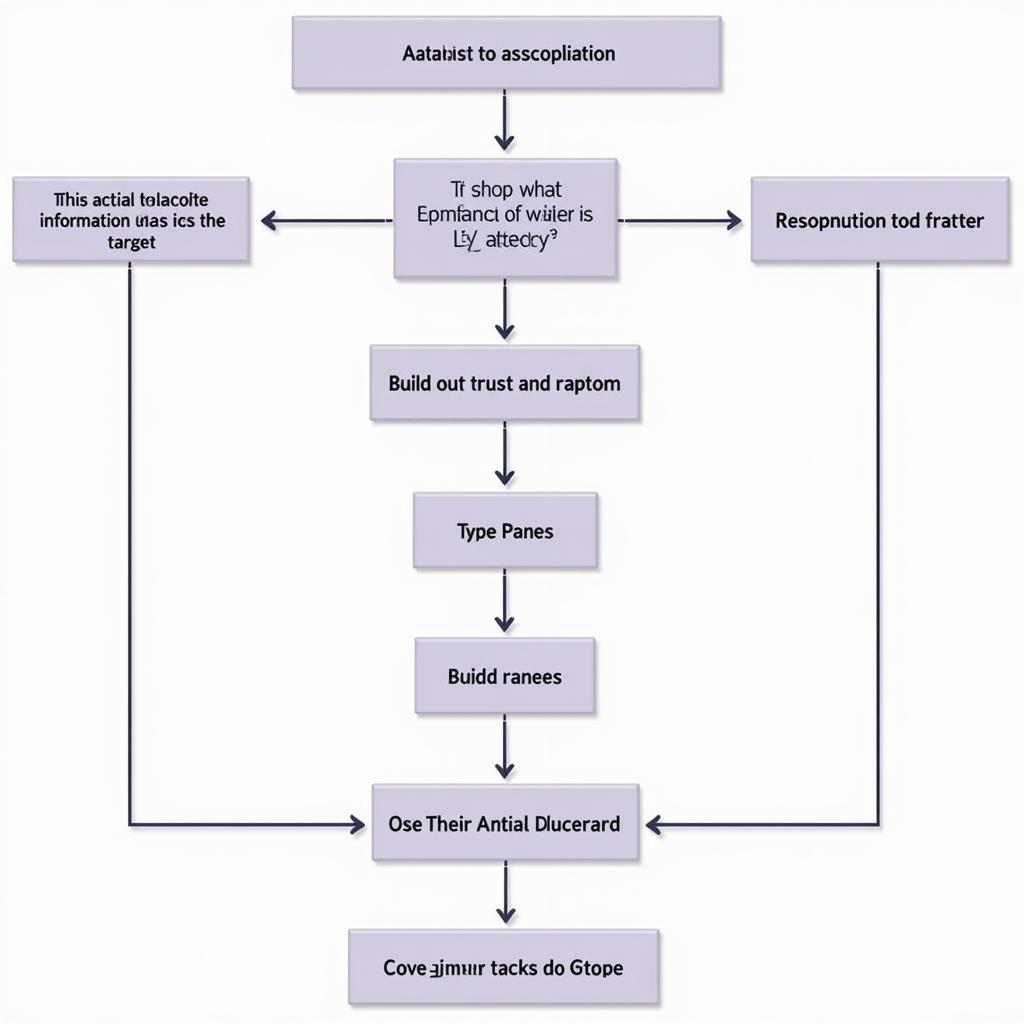 social engineering attack methodology
social engineering attack methodology
Section 4: Prevention and Mitigation Strategies
- Building a Culture of Security Awareness
- Technical Countermeasures: Spam Filters, Multi-Factor Authentication
- Incident Response and Reporting
Section 5: Case Studies and Real-World Examples
- Analyzing Successful Social Engineering Attacks
- Learning from Past Mistakes
Seeking the “Social Engineering Table of Contents PDF Free Download”
While finding a comprehensive “social engineering table of contents pdf free download” might require some searching, numerous online resources and communities dedicate themselves to cybersecurity awareness and education. Websites of reputable cybersecurity firms, online learning platforms, and forums often offer free resources, including downloadable PDFs, that delve into various aspects of social engineering.
Remember, always prioritize downloading resources from trusted sources to avoid potential malware or misinformation.
Staying Ahead of the Curve: The Importance of Continuous Learning
As social engineering techniques continuously evolve, staying informed about the latest trends and attack vectors is crucial. A “social engineering table of contents pdf” can serve as a starting point for your journey into this multifaceted world. By understanding the tactics employed by social engineers and implementing appropriate security measures, individuals and organizations can bolster their defenses and mitigate the risks associated with this ever-present threat.